.webp)
1. Intro
Two weeks ago, Arkham Intelligence announced the largest crypto theft in history. Not the $1.4bn Bybit hack, but something far bigger that's been hiding for five years.
Today, $15.7 billion sits untouched in the hacker's wallets. The theft happened in December 2020, but LuBian Mining Pool never told anyone. The crypto world assumed they'd shut down due to regulatory pressure. They were wrong.
It wasn't a sophisticated social engineering attack or cutting-edge malware. It was something far simpler. From the moment they were created, LuBian’s wallets were doomed. Their “random” generator produced private keys that could be recreated by anyone willing to look closely enough. When someone figured this out and was able to guess all the combinations, $3.5 billion vanished overnight.
The Bigger Picture
This mining pool's catastrophic security failure previews crypto's quantum future.
LuBian's theft shows exactly how crypto's quantum apocalypse could unfold: systematic encryption weakness, mass preparation by attackers, then coordinated execution that drains everything in hours before anyone can react. When quantum computers break current cryptography, the same attack methodology will scale to the entire crypto ecosystem.
History doesn't repeat, but it rhymes. Understanding what happened to LuBian isn't just crypto history, it's a warning about how tomorrow's attacks will unfold if we don't prepare today.
2. Setup
LuBian was a Chinese mining giant that at its peak controlled nearly 6% of Bitcoin's total hash rate; the computational power that secures the entire network. Their mining operations spanned China and Iran, managing billions of dollars in Bitcoin across hundreds of wallets.
Their mining rewards were visible on the blockchain, tagged with identifiers like "lubian.com" and "Buffett." At their peak in late 2020, LuBian's wallets held over 136,000 Bitcoin worth approximately $3.7 billion. Then it suddenly stopped.
LuBian's mining operations went silent in March 2021. No more blocks mined, no more public communications, no explanation. Their website remained online, but the mining pool that had controlled 6% of Bitcoin's security simply vanished.
The crypto community had a ready explanation: China was cracking down on Bitcoin mining. By May 2021, Chinese authorities had banned crypto mining entirely, forcing operations to shut down or relocate. LuBian's disappearance fit perfectly into this narrative.
Most didn't look closer. When a major mining pool goes dark during a regulatory purge, the default assumption is compliance, not catastrophe. And so the largest theft in Bitcoin's history went completely unnoticed.
3. Technical: What Actually Happened
Credit to the Milk Sad security research team who deserve recognition for the systematic cryptographic investigation that uncovered this vulnerability pattern. They go into granular detail across multiple posts: here, here and here.
They published this over a year before the Arkham announcement. Their forensic work revealed a flaw so fundamental it didn't just weaken wallets but made them predictable from birth.
The Random Number Generator That Wasn't Random
LuBian's wallet generation process used a pseudorandom number generator called Mersenne Twister MT19937 to create private keys. In secure systems, this should be seeded with a truly unpredictable number. Instead, the vulnerable implementation seeded MT19937 with a single 32-bit integer from the system clock: a Unix timestamp counting seconds since January 1, 1970.
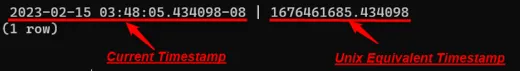
The "random" sequence was fully determined by the exact moment the wallet was created. Same timestamp in → identical "random" output out.
The Mathematical Catastrophe
A Bitcoin private key should have 256 bits of entropy: 2^256 possibilities, more than the estimated number of atoms in the observable universe. LuBian's keys had just 32 bits of effective entropy from the timestamp: 2^32, roughly 4.3 billion possibilities.
Billions of possibilities sounds like a lot until you realize a gaming PC can crack them in hours.
It’s like the difference between a safe that would take longer than the age of the universe to crack and a suitcase lock you can try every combination on during a long layover.
Why These Wallets Were Born Broken
This wasn't a hack in the traditional sense. No breach, no malware, no insider theft. The private keys could be recreated entirely offline by anyone who knew the approximate creation time and replicated the flawed generation process.
It's like a bank vault where the combination is always the same if you know what time the lock was installed. If you can figure out the installation timestamp, you can open any vault using that system.
For LuBian, it meant every wallet created with this process was a ticking time bomb, waiting for someone to spot the pattern, rewind the clock to the creation moment, and recreate the private keys to empty the funds.
And in December 2020, someone finally did.
4. Execution
The Preparation Phase
The attack that drained LuBian didn’t begin on December 28, 2020. It likely started weeks or months earlier, unfolding entirely out of sight.
The first step was mapping the target. LuBian’s mining operations were highly visible on-chain, with block rewards flowing into easily identifiable addresses tagged with lubian.com and Buffett. From there, the attackers could isolate which addresses had been generated by the flawed wallet process.
The attackers built a complete database: every vulnerable LuBian address and its corresponding private key and balance. They pre-built automated scripts to execute hundreds of transactions, all using the same 75,000 satoshi fee.
The Coordinated Strike
December 28, 2020 began like any other day for LuBian. Over $3.7 billion in Bitcoin sat in what they believed were secure wallets.
Then the sweep began.
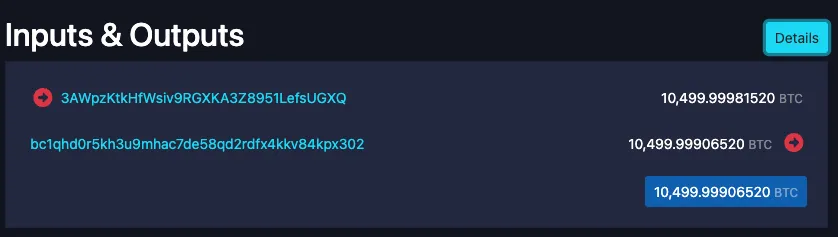
Hundreds of LuBian's wallets began emptying. Transaction after transaction, each signed with the perfectly replicated private keys, systematically swept funds to attacker-controlled addresses. The identical fees across hundreds of transactions made it obvious: this was a preloaded, automated execution, not a manual theft.
The attack lasted approximately two hours. By the end, 127,426 Bitcoin (about $3.5B at the time) had been drained to attacker addresses, while the remaining funds were moved to other LuBian wallets that the attackers hadn't compromised.
The Numbers
- Total BTC stolen: 127,426 Bitcoin
- Value at time of theft: ~$3.5 billion (2020 prices)
- Today's value: ~$15.7 billion
- Attack duration: ~2 hours
5. Aftermath
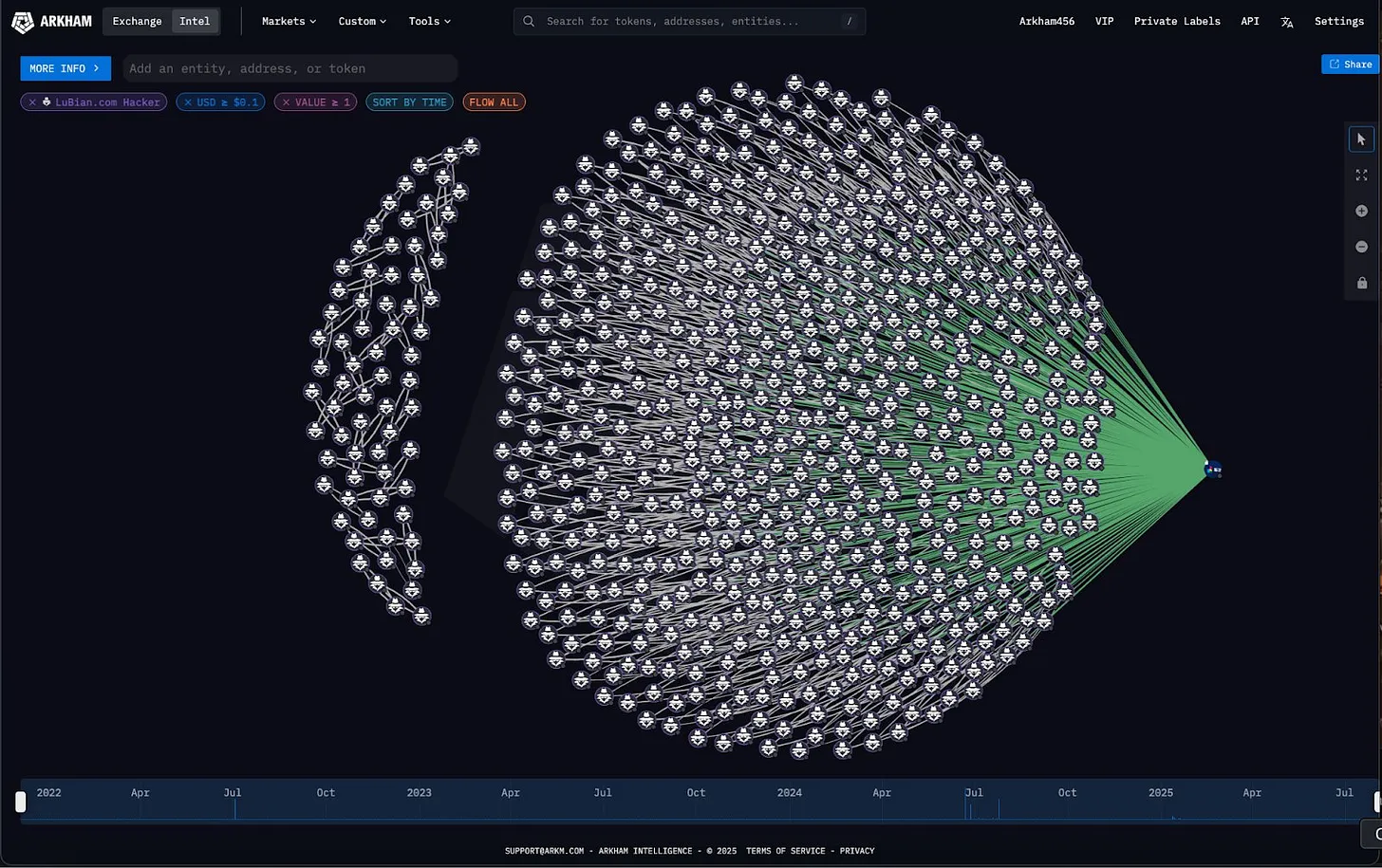
The stolen funds weren't laundered or mixed through complex schemes. Instead, they were consolidated into large addresses. Today, those addresses still hold the Bitcoin, making the unknown attacker the 13th largest Bitcoin holder globally. For reasons unknown, they've never attempted to cash out this massive fortune.
The Realization
By the time LuBian’s operators grasped what was happening, $3.5 billion in Bitcoin was already gone. The human reality of a systematic crypto failure would have hit instantly: panic, confusion, and complete helplessness. These weren’t suspicious logins they could block or pending transfers they could freeze. Every transaction was cryptographically valid, signed with private keys the attackers had recreated. There was nothing to stop.
Mysterious Messages
Afterward, messages appeared on the blockchain using OP_RETURN transactions:
"MSG from LB. To the whitehat who is saving our asset, you can contact us through 1228btc@gmail.com to discuss the return of asset and your reward."


We have no way to know if these desperate pleas came from LuBian themselves or from the attackers who now controlled the same private keys. Both parties had identical access to send transactions from the compromised wallets.
Either way, no one ever responded.
The Cover-Up
LuBian never disclosed the $3.5 billion theft. They quietly shut down operations by March 2021 and moved on.
When the crypto industry noticed 6% of Bitcoin's hash rate had disappeared, the explanation seemed obvious: China's intensifying crackdown on crypto mining was forcing operations to close. LuBian's shutdown fit perfectly into this narrative. And so the largest theft in Bitcoin’s history vanished into the noise.
6. Quantum Blueprint
LuBian’s hack is a preview of crypto’s quantum endgame.
For LuBian, the flaw was a pseudorandom number generator seeded with predictable timestamps. In the quantum future, the flaw will be universal: elliptic curve cryptography broken by Shor’s algorithm. The sequence is the same; a vulnerability hiding in plain sight, months or years of invisible preparation, and then a coordinated strike that empties everything before anyone can react.
The Preparation Advantage
This is the most chilling parallel. Quantum attackers won’t announce their breakthrough. They’ll work in total secrecy, quietly deriving private keys for every major wallet and exchange while the industry operates in blissful ignorance, convinced its cryptography still holds.
From Local to Global Scale
LuBian was one mining pool. One software flaw. 127,426 Bitcoin gone in two hours. Quantum will be different only in scope: every wallet, every chain, every protocol, all vulnerable at the same time. From retail wallets to institutional cold storage, nothing will be outside the blast radius.
Intelligence About the Future
LuBian’s story is a blueprint. It shows that when cryptography fails, the collapse is instant, irreversible, and total. The only difference between 2020 and the quantum future will be scale.
LuBian reveals the terrifying reality of cryptographic failure, what seems mathematically secure can become mathematically trivial.
7. Solutions: Building Defenses for Both Timelines
The Speed Problem
LuBian's theft exposed a fundamental flaw in crypto security. When private keys are compromised at scale, humans are powerless to respond in time.
From the moment the drainage began to complete emptiness: two hours. No emergency board meeting, or manual human coordination could have stopped the systematic sweeping of funds.
Attack timelines are compressing to machine speed while human response time remains frustratingly analog.
Immediate Protection: Automatic Asset Extraction
The solution isn't faster humans: it's removing humans from the critical path entirely.
Automatic Asset Extraction (AAE) continuously monitors for funds going to unauthorized destinations and immediately sweeps those assets to safety ahead of attackers. No human decision-making delays, just automatic response.
If AAE had been monitoring LuBian's systems, the system would have been able to respond to the systematic outflows in real-time and move funds to safety instead of watching $3.5 billion drain away.
Long-Term Preparation: Post-Quantum Cryptography
Automatic extraction buys time, but it’s not enough. Current elliptic curve cryptography has a mathematical expiration date. Once quantum computers cross the threshold, today’s keys will be obsolete overnight.
NIST has already published quantum-resistant algorithms, but full migration will take years. Quantum progress is moving faster than our defenses and the window for an orderly transition is closing fast.
Waiting for the first attack is waiting for a LuBian-scale disaster, only this time at global scale.
8. Conclusion
The Pattern
LuBian's collapse was a glimpse of what could come for everyone in crypto. Attackers will find the weakest link, quietly map it, and strike at machine speed to systematically drain funds faster than humans can respond.
Quantum computing will follow the same playbook: vulnerability → preparation → execution, everywhere at once.
The Choice
The lessons are simple but urgent: match the speed of defense to the speed of attack, and cryptography must stay ahead of computation. Automatic Asset Extraction can close the speed gap today. Post-quantum migration can close the cryptographic gap for tomorrow.
Final Thought
LuBian trusted the system clock, those predictable Unix timestamps that turned their "random" private keys into a countdown to disaster. Crypto can’t afford to make the same mistake with today's encryption. The clock is ticking.
Want to keep up to date with Circuit? Sign up below
Related Posts
Discover more about Circuit’s latest News and Research

Lloyd's First Digital Asset Bet
From clustered loss events to institutional demand, learn how Circuit Security and Lloyd’s are transforming digital asset insurance and risk pricing.

How The $128m Balancer Exploit Happened
On November 3rd, 2025, an attacker weaponized Balancer’s rounding errors and complex features to manipulate token prices and steal $128 million across eight blockchains - all within two hours.

Inside the SEC’s Crypto Task Force Roundtable
No policy emerged, but the SEC’s private roundtable exposed how crypto’s core principles clash with outdated financial rules-and why new regulatory frameworks are needed.
Built by experts who’ve made digital assets safer, and now, recoverable
We believe asset recoverability is table stakes for the next era of digital assets.





