
1. Introduction
Yesterday, ~$1.4bn was stolen from Bybit. This is the largest hack in crypto history, completed by Lazarus Group, North Korea’s state sponsored cyber-crime unit.
It wasn't a hack of keys or passwords, it was something much more sophisticated. Attackers tricked multiple employees into approving a legitimate blockchain transaction. This seemingly routine transaction had a hidden flaw. A single parameter, buried in the transaction data, flipped from 0 to 1. That tiny change transferred full control of Bybit’s wallet to the attackers.
2. The Setup – How Crypto Exchanges Protect Funds
Exchange Operations
Crypto exchanges don’t store all funds in a single wallet. Instead, they separate them into many different cold and hot wallets for security, with the majority of assets kept in cold storage.
- Cold storage is like a bank vault. It generally involves a physical device kept offline which requires multiple layers of approval to move funds. You can learn more about the multiple layers of protection in digital asset security here.
- Hot wallets are like a cash register. They are connected to the internet for faster transactions.
When an exchange wants to perform day-to-day activities they transfer assets from cold storage to a hot wallet. Think of it like moving funds from the secure vault to a tellers drawer.
This is the routine operation Bybit was doing, something they had done countless times before. But this time it didn’t go to plan.
Bybit’s Set-Up
To reduce single points of failure, Bybit used Safe smart contract wallets instead of relying on a single private key.
Smart contract wallets are controlled by pre-programmed rules rather than a single owner. Safe’s code is public and audited, allowing anyone to view and verify how it works.
Safe requires multiple people to approve any transaction, just like a bank vault needing three different keys to open. This prevents any single person or compromised key from moving funds.
However, while this setup removed private key risks, it introduced complexity which the attackers exploited.
3. The Hidden Detail That Changed Everything
To understand the attack, we first need to break down how Safe transactions work.
Blockchain Transaction
A standard blockchain transaction is straightforward. When setting one up, you have to specify:
from: Who is sending fundsto: Who receives themvalue: How much is being sentdata: Additional instructions if interacting with a smart contract
Safe Transaction
Safe transactions introduce extra parameters you have to specify. One critical parameter is operation.
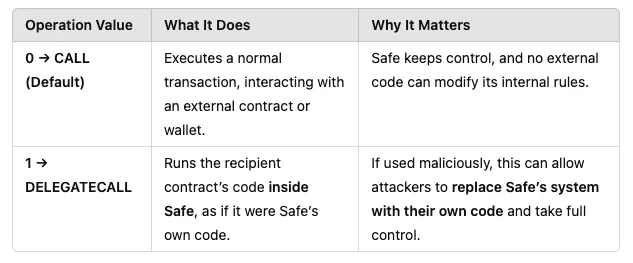
When operation = 0 it executes a normal transfer of funds.
Setting operation = 1 it flicks a switch to allow an action called delegatecall. This allows the Safe wallet to run a different smart contract’s code as if it were it’s own.
Think of it like this:
- You sign off on a bank transfer. But a hidden checkbox in the fine print also adds someone else as a joint account holder with limited permissions.
- But because they now exist inside your account, they could escalate their permissions and take full control.
This is exactly how delegatecall was exploited in the Bybit hack.
4. The Attack
On February 18th and 19th, the attacker deployed 2 malicious contracts, designed to be executed later. These contracts contained hidden code to allow the attacker to drain funds when executed. More details here.
On Feb 21st, when Bybit employees went to approve what looked like a routine transfer, they all checked the same user interface. According to Bybit, everything appeared normal.
But unknown to them the interface had been compromised, replacing the seemingly routine transaction with a new one. And hidden in that transaction were critical changes that reprogrammed the Safe wallet’s rules.
The Details
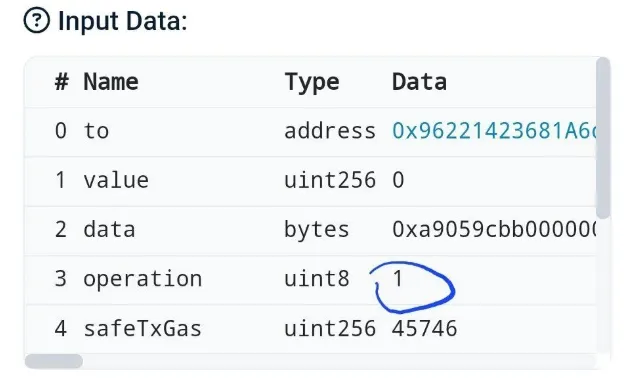
The approvers unknowingly approved a different transaction which included:
operation =1, enablingdelegatecallto:set to the attackers first malicious contract addressdata:containing the address for the second malicious contract, which included the code to drain the funds
These attackers were sophisticated. They knew that the limited permissions of delegatecall alone wouldn’t let them steal the funds. So they executed a two-step takeover.
- The first malicious contract was used to change the Safe wallet’s settings, swapping out its original code for their own
- The second malicious contract became the new Safe’s code, giving the attackers control.
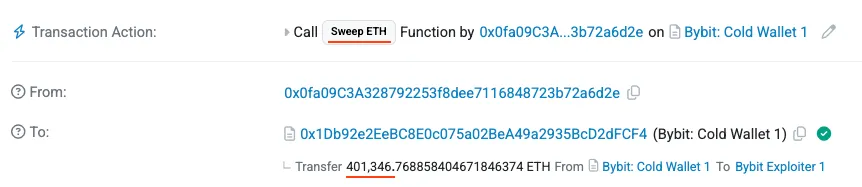
The attackers then swept all the funds to their own wallet.
Going back to our bank transfer analogy:
- After the hidden fine print added someone as a joint account holder, they then used the limited access to replace the instructions controlling your account settings with their own.
- After that they were able to withdraw everything.
Why Was The New Transaction Signed?
The exact method used to compromise the interface remains unconfirmed, and it is unclear whether it was due to a phishing attack, device compromise, or manipulation of Bybit’s signing process.
Regardless of what occurred, the malicious transaction was signed, enabling the attackers to access Bybit’s wallet using their own malicious contract.
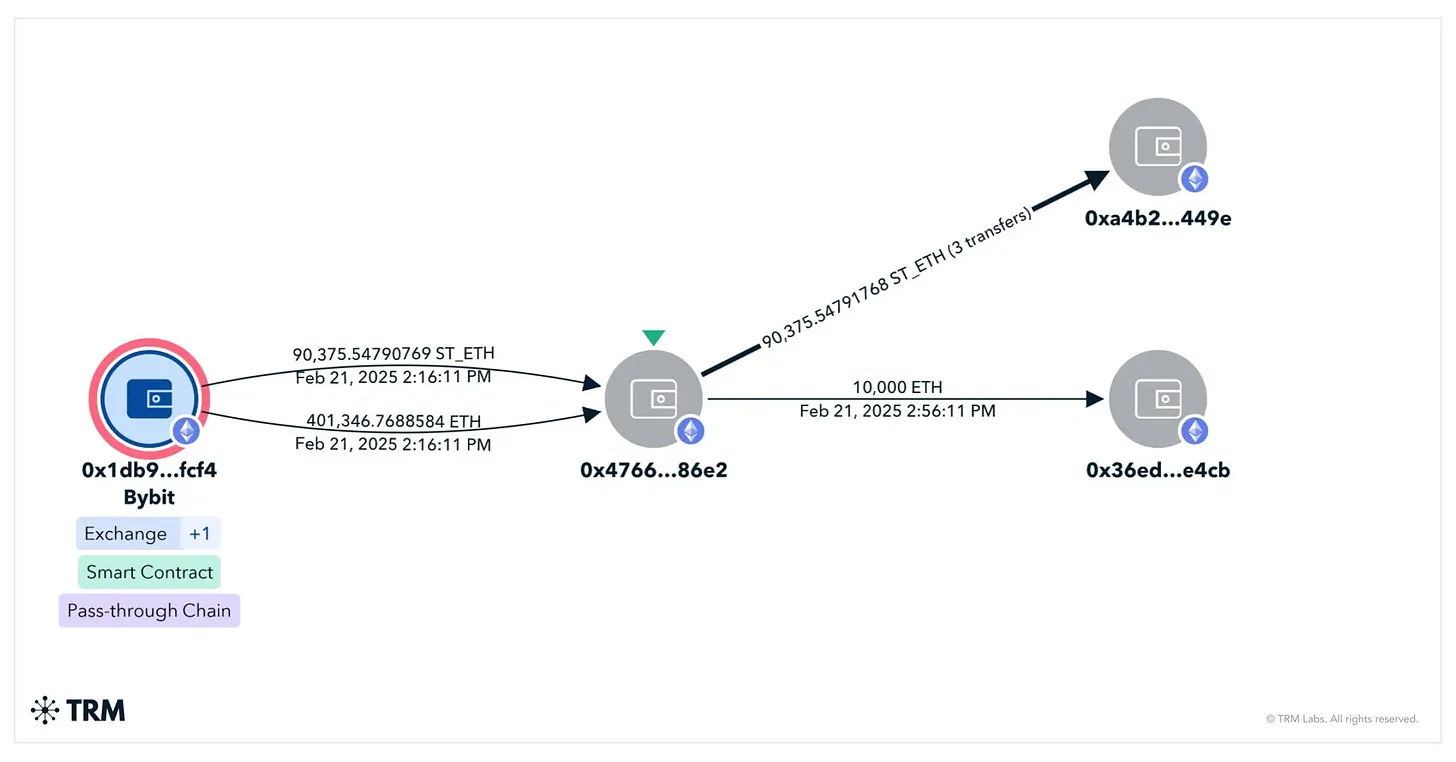
Within minutes, the attackers started sweeping the funds to their own addresses, draining ~$1.4 billion.
5. The Aftermath
Immediately after the attack, blockchain analysts began tracking the stolen funds. The attribution to North Korea’s state-backed Lazarus Group was quickly confirmed, with their wallet addresses linked to previous large-scale exchange hacks.
The $1.4bn in stolen assets were quickly dispersed, with the attacker’s wallet initially splitting the funds across over 50 different addresses to obfuscate the trail. There are now over 900 address connected with the hack.
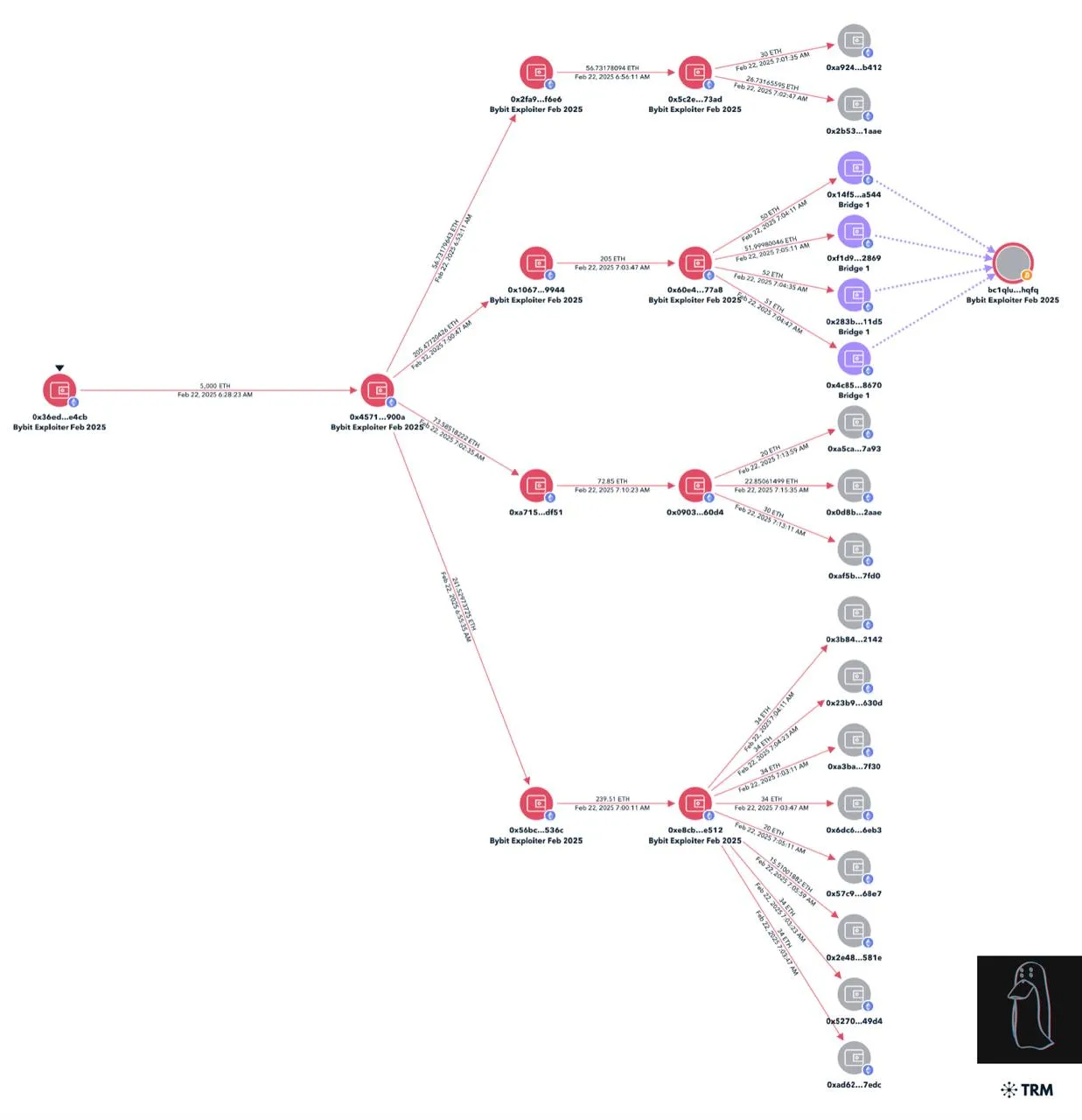
Where the Funds Are Going Next
The attackers’ next step will be to erase their tracks before cashing out, using tactics like:
- Bridging: Moving assets across blockchains to break transaction history and make them harder to trace. Lazarus has used this method in the $625m Axie Infinity hack to escape detection.
- Mixers: Blending funds with others to erase ownership trails. Lazarus has previously used mixers like Sinbad.io to disguise transactions.
Bybit’s Response
Bybit’s responded quickly and transparently. CEO Ben Zhou issued an immediate public statement, confirming the attack and ensuring withdrawals remained open.
Despite the severity of the attack, Bybit processed over 350,000 withdrawal requests in a short period, ensuring customers were not locked out of their funds.
The exchange also coordinated with industry partners to trace and freeze stolen assets. Some of the funds have already been flagged and frozen, with efforts ongoing to recover more.
What Happens Next
Law enforcement agencies and blockchain analytics firms are actively tracking the attacker’s wallets, monitoring for any attempts to convert funds into fiat. Their goal: freeze assets before they disappear into laundering networks.
This attack is still unfolding. As I write this, the stolen funds are bouncing across multiple wallets and networks, and security teams are racing to freeze them.
6. Conclusion
Was the Bybit hack preventable? Yes.
Additional levels of control and external verification could have flagged the malicious transaction, even if Bybit’s signing interface was compromised.
However, the real lesson from the Bybit hack isn’t just about one exchange and what went wrong. It’s about the broader operational risks in crypto.
Shifting from the frame of mind of “don’t get hacked” to “when an attack happens, how do we mitigate damage and respond effectively” is important as an industry to embrace going forward.
Traditional finance operates on “assume failure” mode. It builds layers of risk management, reserves, and response plans to minimize damage when things go wrong. Crypto needs to adopt the same practices industry wide.
No system is ever hack-proof. Attackers will always adapt, and once one vulnerability is fixed, another will be found. The real goal isn’t perfect security, it’s making exploits so difficult, costly, and detectable that they become impractical.
Security now means layering protections, enforcing stricter controls, and preparing to respond rapidly to events as they occur in real time.
With regulatory clarity on the horizon, operational risks will become the biggest challenge to digital assets to gain mass adoption. Lets work together to prevent that from happening.
Attacks like this won’t stop. But with better security controls, they don’t have to win.
Want to keep up to date with Circuit? Sign up below
Related Posts
Discover more about Circuit’s latest News and Research

Lloyd's First Digital Asset Bet
From clustered loss events to institutional demand, learn how Circuit Security and Lloyd’s are transforming digital asset insurance and risk pricing.

How The $128m Balancer Exploit Happened
On November 3rd, 2025, an attacker weaponized Balancer’s rounding errors and complex features to manipulate token prices and steal $128 million across eight blockchains - all within two hours.

Inside the SEC’s Crypto Task Force Roundtable
No policy emerged, but the SEC’s private roundtable exposed how crypto’s core principles clash with outdated financial rules-and why new regulatory frameworks are needed.
Built by experts who’ve made digital assets safer, and now, recoverable
We believe asset recoverability is table stakes for the next era of digital assets.





