
Last week, the White House formally endorsed digital assets, marking a decisive end to years of regulatory uncertainty and validating blockchains as legitimate infrastructure for the modern financial system.
For major corporations and financial institutions that have been waiting on the sidelines, this regulatory clarity is the green light they have been waiting for.
In the report, the White House also acknowledged another reality: institutions still face major risks with digital assets. But beyond financial regulation and custody frameworks, it is recognition that digital asset cybersecurity is no longer just a subset of general cybersecurity, but a rapidly advancing discipline in its own right.
From Regulatory Clarity to Operational Risk
With regulatory barriers now falling away, operational security becomes the critical frontier. The focus shifts from "can we use digital assets?" to "how do we secure them at enterprise scale?"
The White House explicitly called for technical standards in digital assets to create “industry norms" and solve coordination problems (pages 39-41). The NIST Cybersecurity Framework has been the gold standard for cybersecurity for over a decade, and recent technological advances now make comprehensive application to digital assets possible.
What we're going to do is answer that call by showing how to apply the NIST CSF framework to address the institutional risks the White House identified, demonstrating how emerging digital asset security technologies provide systematic coverage across all five pillars.
For executives and risk managers evaluating digital asset strategies, understanding these developments is essential for implementing security that matches the sophistication of the threats.
Note: The White House report addressed both key management and smart contract security. This piece focuses on key management and custody, the foundational layer institutions need to establish first. Smart contract security represents a separate, specialized domain deserving its own analysis.
1. What They Got Right
Risk Analysis
The White House identified multiple risk categories for digital assets, including custody, fraud, privacy, and operational risks. Among these, key loss and key compromise stand out as the most fundamental threats; “loss or theft of a private key generally results in the loss of digital assets” (page 38).
The Scale of the Problem
The numbers validate their concerns. Approximately $350 billion in Bitcoin has been permanently lost due to key mismanagement. Unlike traditional finance where account access can be restored through identity verification, lost private keys mean lost assets forever.
Key theft presents equally devastating consequences. Private key compromises were the single most damaging attack vector in 2024, causing $930 million in losses (48% of total hack value), making it the most persistent threat facing institutions.
Unlike traditional financial systems where fraudulent transactions can often be reversed, blockchain transactions are immutable. Once funds transfer to an attacker's wallet, recovery through conventional means becomes extremely difficult, with only 4.2% of stolen assets recovered after loss in the first half of 2025.
The speed of these attacks makes traditional response effectively impossible. Hackers can move funds in as little as 4 seconds, while the fastest full laundering process takes under 3 minutes. The window for action closes almost instantly.
These represent existential operational risks that would be unacceptable for any institutional operation. The scale of historical losses demonstrates that digital asset security failures can be company-ending events.
These risks primarily apply to institutions operating on public blockchains with bearer digital assets. Permissioned networks, tokenized securities with traditional clearing mechanisms, and assets with built-in controls (like USDC's freeze functionality) may have different risk profiles and recovery mechanisms. However, institutions operating on public networks or with truly decentralized assets face these immutability constraints directly.
The White House deserves recognition for highlighting these risks with appropriate gravity. They understand the stakes and correctly identify what institutions need to protect against.
2. What They Recommended: Solid Foundation, Incomplete Picture
The White House recommendations focus on proven custody approaches (Page 33):
- Cold storage systems keeping assets offline and disconnected from networks
- Multi-signature wallets requiring multiple approvals for transactions
- Multi-party computation (MPC) distributing key generation and signing across multiple parties
These technologies form a solid foundation and belong in any institutional digital asset security setup. The recommendations align well with established cybersecurity principles.
Here's how we approached analyzing their coverage. The NIST CSF recognizes five essential functions for comprehensive cybersecurity:
- Identify: Understanding assets and risks
- Protect: Implementing safeguards and access controls
- Detect: Monitoring for security events and anomalies
- Respond: Taking action when threats are detected
- Recover: Restoring capabilities after incidents
The NIST CSF is intentionally principle-based rather than prescriptive; it defines what security functions institutions need but doesn't specify how to implement them. For digital assets, this means institutions must identify which specific technologies deliver each capability.
When mapped against the framework, the White House recommendations excel in two areas: Identify (risk assessment and asset categorization) and Protect (safeguards and access controls).
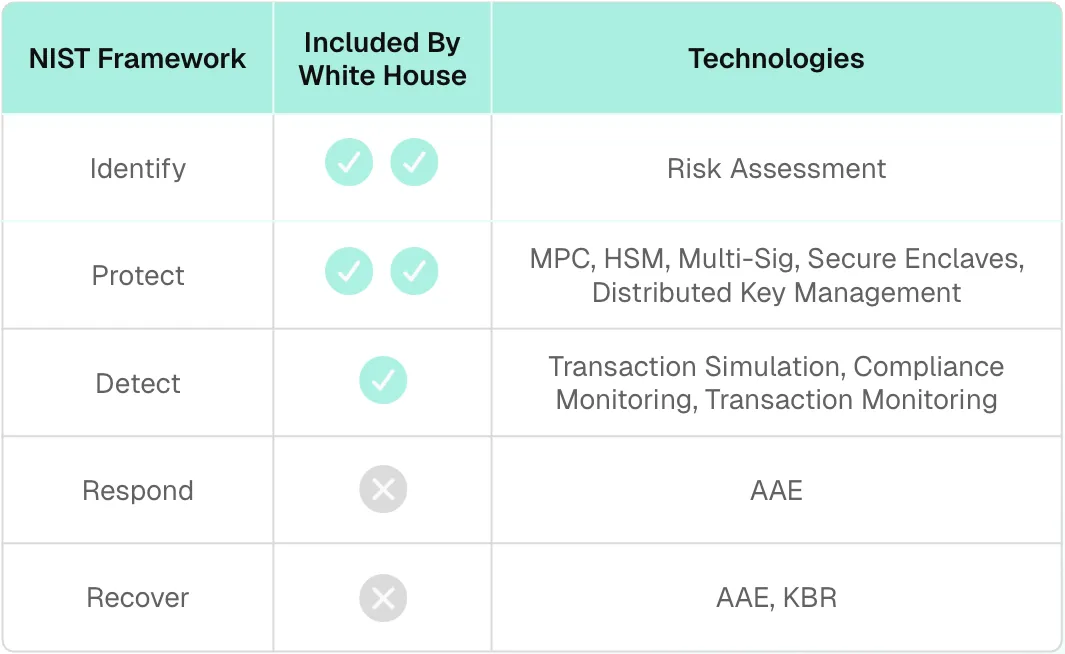
However, while the report mentions some detection capabilities like transaction simulation tools (page 121), it provides limited coverage beyond that and virtually ignores response and recovery entirely. This represents the gap that recent technological advances in digital asset security have been designed to address.
3. What's Evolved: Modern Digital Asset Security
Digital asset cybersecurity has rapidly evolved beyond traditional custody thinking. New technologies have emerged that directly address the key loss and key compromise risks the White House identified.
Here's what complete institutional coverage looks like today:
Identify & Protect (White House Covered)
- Risk assessment and threat landscape mapping
- Multi-signature wallets
- Multi-party computation (MPC)
- Cold storage systems
Modern protection capabilities have expanded to include:
- Hardware security modules (HSMs) for tamper-resistant key storage
- Advanced secure enclave technologies
- Distributed key management systems
Detect
Digital assets operate in an always-on, globally accessible environment requiring continuous monitoring:
- Real-time transaction monitoring systems scan for suspicious patterns, unusual destinations, or policy violations across multiple blockchain networks simultaneously.
- Transaction simulation technology analyzes proposed transactions before execution to identify potential risks, malicious contracts, or unexpected outcomes.
- Compliance monitoring systems that screen transactions against sanctions lists and regulatory requirements in real-time.
Unlike traditional banking systems that operate during business hours, blockchain networks never sleep. Detection systems must provide 24/7 coverage across multiple networks and asset types.
Respond
When threats are detected, institutions need immediate response capabilities:
- Automatic asset extraction systems (AAE) can instantly move assets to safety when threats are detected, without waiting for human intervention or complex approval processes.
Response speed is critical in digital assets. Unlike traditional fraud scenarios where banks can halt suspicious transactions, blockchain transactions are irreversible once confirmed. The window for effective response is often measured in seconds, not minutes.
Recover
Even with comprehensive protection, detection, and response, institutions need guaranteed recovery capabilities:
- Automatic asset extraction (AAE) can reclaim assets even in scenarios involving compromised keys or system failures, restoring operations immediately.
- Key backup and recovery (KBR) systems provide secure backup mechanisms that ensure key material can be restored even after catastrophic system failures.
Recovery serves as the final technology safety net. While traditional finance offers transaction reversals and deposit insurance, digital assets require recovery mechanisms designed specifically for immutable blockchain systems.
4. Why Complete Coverage Matters
Each capability addresses different failure modes that institutions will inevitably encounter:
- Protection prevents the majority of routine threats but cannot stop all sophisticated attacks or account for human error.
- Detection provides early warning when protection measures are being probed or compromised, buying crucial time for response.
- Response minimizes damage when threats break through protective measures, potentially saving institutions from the catastrophic losses identified.
- Recovery ensures business continuity even after worst-case scenarios, providing the safety net for institutional operations.
These capabilities work together. Weakness in any single area undermines the entire security posture. An institution with excellent key management but no threat detection might not realize they're under attack until assets are already gone. Similarly, sophisticated monitoring without automated response capabilities leaves institutions watching helplessly as attacks unfold in real-time.
As adoption accelerates, institutions with incomplete coverage will face higher insurance costs, regulatory scrutiny, and potential exclusion from digital asset opportunities
The White House correctly identified that digital assets require new security thinking. The specialized field has developed that thinking and built the technologies to implement it.
The Complete Picture
As Wayne Gretzky said, you need to skate to where the puck is going, not where it's been. The White House explicitly called for applying frameworks and standards to digital asset security and these may well become regulatory requirements in the future.
Smart institutions are getting ahead of these potential requirements by evaluating their current position. How well does your organization rank in terms of NIST framework implementation across all five pillars?
As regulatory clarity accelerates adoption, operational security excellence becomes the differentiator between organizations that capitalize on digital assets and those that become cautionary tales.
What This Means for Institutions
As regulatory clarity accelerates institutional adoption, operational security excellence becomes the differentiator between organizations that successfully capitalize on digital assets and those that become the cautionary tales the White house is trying to prevent.
Moving Forward
We're mapping how existing technologies and vendors measure against the complete NIST framework. Subscribe for our upcoming analysis showing exactly where different solutions fall, helping institutions evaluate their security options systematically.
Want to keep up to date with Circuit? Sign up below
Related Posts
Discover more about Circuit’s latest News and Research

$4.8M In Crypto Lost To A Press Photo
South Korea's tax authority published a seed phrase in a press photo. Police lost 22 Bitcoin from a vault. A third agency is investigating vanished seized crypto. Three custody failures, weeks apart, zero technical sophistication required. We break down the operational gaps and what institutional operators should take from it.

Lloyd's First Digital Asset Bet
From clustered loss events to institutional demand, learn how Circuit Security and Lloyd’s are transforming digital asset insurance and risk pricing.

How The $128m Balancer Exploit Happened
On November 3rd, 2025, an attacker weaponized Balancer’s rounding errors and complex features to manipulate token prices and steal $128 million across eight blockchains - all within two hours.
Built by experts who’ve made digital assets safer, and now, recoverable
We believe asset recoverability is table stakes for the next era of digital assets.




